Anyone who’s been to five minutes of an interviewing or investigator’s school, or who has taken a shoplifting call, knows the power of asking the right questions. “Yes or no: Did you steal?” vs. “So tell me what happened today” are two different ways to phrase the same question, which will each probably yield totally different answers.
The same is true online.
In 2014 the FBI put out a document warning about advanced search techniques. This technique is known as “google hacking” or “google dorking.” (Yes, I just used dorking as a verb, and it’s not even a real word according to my spell check.)
Well known fact about Google: It’s really great at finding stuff. Fun fact about Google: You can use it to hack. It’s so good at finding stuff, you can actually ask the right questions and get super specific and detailed information, including lists of passwords, credit card numbers, employee tax records, and the like. Given the right knowledge of what to ask for, you can even look for sensitive information that isn’t supposed to be publicly available.
Oh! And there’s already multiple websites running around that tell you exactly what to search for, and what you’ll find. Exploit-db.com has a list of search queries you can run through Google and sit back and watch what pops up. (Click here to see, at your own risk of course.) Keep in mind this is so old, their database of search terms that find passwords goes back to 2003. Yes, this is 13 years old, and we’re finally talking about it.
Now obviously that’s a little scary and concerning. But this can also be quite effective with investigations. Imagine you’re looking for someone’s really unique screen name, or street name, and you know they’ve gone by this moniker their entire life. Go to Google, and type in their unique screen name. Let’s use my twitter handle, CyberBloodhound. (Please note that you need to put in quotes to tell Google, “Hey, look for ONLY THIS TERM EXACTLY AS IS,” otherwise Google will be helpful and maybe get you a lot of other pages that just have “bloodhound” and “cyber” in it.)

And just like that we found a few unrelated things, but the first hit was my Twitter account (which you should totally go check and follow for more neat ideas and articles).
Let’s say you know Cyberbloodhound posts on a particular website, maybe CalibrePress.com? You can further specify what to look for by narrowing down a particular site using this fun operator: “site:” or “inurl:”. Here’s how the query would look:
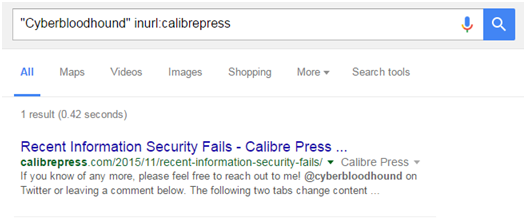
“Cyberbloohdound” inurl:calibrepress
I just told Google, “Only find Cyberbloohound spelled EXACTLY like that with ‘calibrepress’ in the webpage name.” (A webpage’s address is called a Uniform Resources Locator—URL.)
Or:
“Cyberbloodhound” site:Calibrepress.com
I just told Google, “Only find Cyberbloohdound spelled EXACTLY like that when the site is called ‘calibrepress.com’.”
Here are the search results: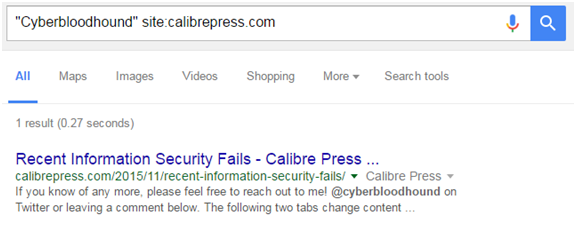
By the time you’re reading this article, Google will have already indexed this page and added it to its list. There will now be two pages when you do this search.
For Security Testing
One of the important things to note is that a lot of sensitive information has been leaking out thanks to Google. The website that I linked to earlier, publicintelligence.com, has a lot of information that they find posted in various places online. Their most recent posting (as of this writing) is a cyber bulletin put out to universities by the MS-ISAC (information/intelligence sharing organization). They even say they got it from the Missouri Department of Higher Education.
And here, dear reader, is where I reach a bit of an ethical dilemma.
The information is out there. Using the resources I’ve already pointed you towards, you can spend another five minutes mixing and matching, figuring things out, and pretty soon you can start finding excel spreadsheets with passwords and logins for an entire company.
The blue parts are what I redacted.
As you can tell by this list, a bad guy can breach a ton of important stuff about this organization, including their payroll management. Some of the account names were so sensitive I had to block that stuff completely. Oh, and remember my article on passwords? They should totally read that.
Now this organization, and the other 13,400 I got with that search, don’t need people like me writing articles like this highlighting their vulnerabilities and giving the bad guys a direct link to the passwords to their PAYROLL MANAGEMENT account! We’re faced with a serious problem–do you show the vulnerabilities exist and jeopardize those organizations? Or do we keep our mouths shut and hope nothing bad happens?
We’ve been doing the latter, and it’s clearly not working.
And, no, they also don’t need to be the victim’s of a data breach to learn a hard lesson.
What they (and you) do need is a person to check their vulnerabilities, look for their stuff online, and find it before the bad guys do. And if you don’t think it’s a problem law enforcement on every level—think again. This is something that’s been done to find sensitive law enforcement, defense, and national security information that’s been leaked online.
Bringing It All Together
Google hacking is an incredibly powerful way to find information, for both good and bad. This is one of those ways that we can start to embrace and utilize the offensive capabilities of the internet instead of just fearing them. So go dorking for good, not evil!











0 Comments